The threat of fraud with synthetic identities has become a growing issue. The nature of this fraud, in which fraudsters use a combination of real and fake information, makes it very difficult for financial institutions (FIs) to combat.
Read on to discover what a synthetic identity is, how it works, and why it’s difficult to detect and prevent.
What is a Synthetic Identity?
A synthetic ID is an identity made of a combination of actual and fictitious information. They use authentic and falsified personally identifiable information (PII), such as names, addresses, and Social Security numbers (SSNs), forming an entirely new identity that is not associated with a real person.
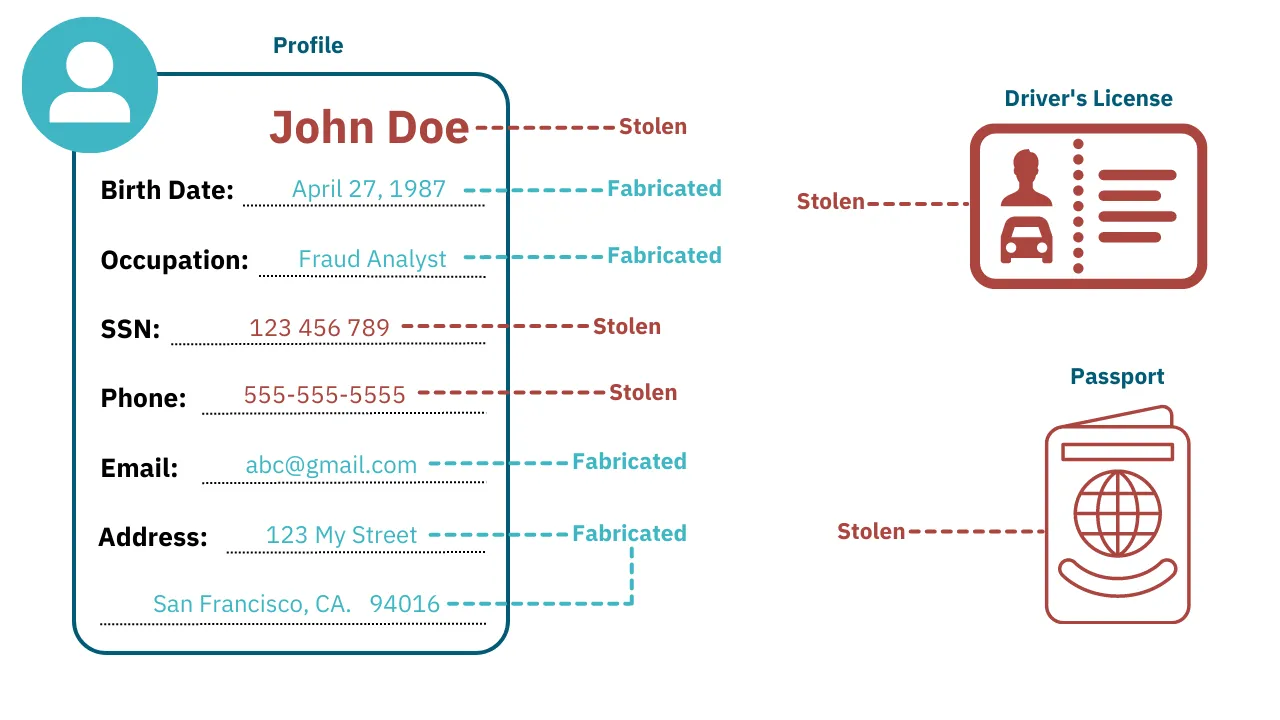
While the synthetic identity is not linked to a real person, they often use real credentials; and sometimes even impersonate a legitimate person.
What Pieces of Information are Used for Synthetic IDs?
To properly protect against synthetic ID fraud, it’s essential that individuals and organizations understand what fraudsters use to create these identities.
Synthetic IDs are a mix of both legitimate (albeit stolen) and falsified information, and can be made up of some or all of the types of information below:
- Stolen ID documents: Legitimate documents that have been stolen from another individual. These are often a cornerstone of synthetic ID theft, as a legitimate piece of documentation lends significant credibility to the identity during verification.
- Stolen personal information: Other personally identifiable information that has been stolen from another individual. These offer added credibility during identity validation processes, as certain information will pass KYC verification.
- Falsified personal information: Entirely fabricated information, designed to fill out the synthetic identity so it appears to be legitimate.
- Tax information: Tax documents have a trove of personal information, and can even be used by fraudsters to make false claims on the victim’s behalf.
- Medical information: Private medical details can be leveraged to round out a synthetic ID, acquire prescription drugs, or even to file fake insurance claims.
While synthetic IDs can be built using varied pieces of information, many rely on a valid SSN (that’s been stolen from a real person). A legitimate Social Security Number (SSN) will pass many identity verification checks, making it a crucial component of most synthetic IDs.
How Fraudsters Obtain Credentials for Synthetic IDs
Theoretically, fraudsters can get credentials from anywhere to create a synthetic ID, but it’s unlikely that they stumble across personally identifiable information just lying about. Typically, fraudsters seek out this information in the same places.
While savvy fraudsters may collect their own credentials when creating synthetic IDs, new and unseasoned fraudsters look to buy this information through online marketplaces. Most commonly, fraudsters seek this out on the dark web, but an increase in amateur fraudsters (who don’t know how to access the dark web) are looking to deep web marketplaces, where stolen personal information can be bought and sold in traditional retail fashion.
Some fraudsters even leverage the use of AI and machine learning technology to bypass identify verification checks using tools like deep fakes. Fortunately, with the right systems in place, teams can prevent even this.
How to Stop Synthetic IDs
It’s incredibly challenging for financial institutions to stop synthetic IDs. They consist of seemingly legitimate information that can pass weak KYC and identity verification checks. They even exhibit behaviors of legitimate accounts and can therefore operate for long periods of time undetected.
Despite the challenges, there are ways to stop synthetic identities from thriving:
Identity Verification
Authentic, government-issued IDs are hard to fake, so verifying ID documentation is an essential step in onboarding new users. Revisit user ID documentation periodically to ensure you collect updated versions throughout the user’s life.
Biometric Authentication
A form of user authentication, biometric authentication uses technology to validate a user's biological characteristic(s). Typically, it involves verifying a user's fingerprint or facial image. The advantage to these tools is that they force the user to validate that they physically exist and that they are who they say they are. It creates an added layer of security and protection for customers that is difficult to fake, and similar in practice to tools like multi-factor authentication.
Payment Screening
A lot can be gleaned from customer behavior. Monitoring transactions for anomalies is a great way to alert your team of potential instances of synthetic ID fraud; isolating fraudsters and victims alike. Screen for specific patterns and investigate suspicious activity to find synthetic IDs being used on your platform.
Eliminate Synthetic Users and Protect Against Fraud
Synthetic IDs are extremely difficult to detect, as they use legitimate credentials that will pass validation and don’t behave with the same urgency as other types of fraud (making it much harder to detect anomalies).
While it’s important to employ rigorous customer onboarding to verify users identities, that won’t be enough to root out synthetic IDs. You’ll also need high-quality transaction monitoring with customizable rules, enabling teams to build alerts that detect even the most adept instances of identity theft.
Quite frankly, without a high-quality AML and fraud detection solution, it’s impossible to tackle more serious threats like synthetic identities. Rule-based engines that can be finely tuned to detect minute anomalies in behavior can significantly reduce fraud losses.
Learn more about Unit21
Unit21 is the leader in AI-powered fraud and AML, trusted by 200 customers across 90 countries, including Green Dot, Chime, and Sallie Mae. One unified platform brings detection, investigation, and decisioning together with intelligent automation, centralizing signals, eliminating busy work, and enabling faster responses to real risk.


