

As digital marketplaces gain popularity and more users flock to their services, so too do fraudsters. As organizations improve security measures, fraudsters find new ways of skirting these protections.
To beat modern customer onboarding and monitoring checks, fraudsters are using synthetic IDs. With a combination of legitimate and fake information, this form of identity theft is often harder to track and trace.
To help, we explore:
First, let’s explore what synthetic identity fraud is and how it relates to the broader crime of identity theft.
Synthetic identity fraud, or synthetic identity theft, is any fraud where a synthetic identity is used. It’s often perpetrated by criminals as a means of performing criminal activity anonymously, and for passing weak identity verification checks.
Most commonly used for eCommerce and online fraud, synthetic identity theft allows criminals to create an entirely false identity, backed with a portion of legitimate credentials. Since this type of fraud uses a variety of legitimate credentials, it can be challenging for organizations to detect.
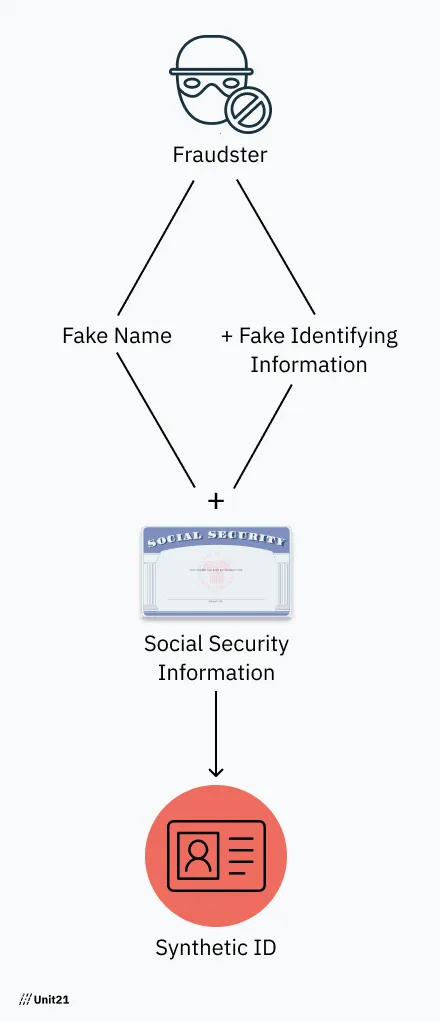
These fake identities typically rely on a real Social Security number (SSN) and other fake credentials, including a name, date of birth, email address, phone number, and more. While synthetic IDs can contain a number of legitimate (but stolen) credentials, they typically rely on a valid SSN, as these give criminals the best chance at passing customer due diligence and KYC checks during onboarding.
As digital eCommerce and payment processors grow in popularity, criminals flock to exploit a system with weak regulations - and seemingly weak protections against fraud. The total cost of synthetic identity fraud was expected to reach $2.5 billion by the end of 2022, and could double that (reaching $5 billion) by 2024.
The problem isn’t stopping anytime soon; and with the use of synthetic IDs on the rise, it will be impossible to mitigate fraud losses without tackling this type of fraud. Businesses that want to keep fraud losses low need to have systems in place to detect and prevent synthetic identity fraud.
Synthetic identity theft is a kind of fraud in which fraudsters use a mixture of fake and authentic information, often stolen, to establish a fictitious identity. This new identity is used to open fraudulent accounts with financial institutions or other entities to make illegal transactions.
Any time a synthetic ID uses at least one stolen credential from a legitimate person, it’s a form of identity theft.
Synthetic vs Traditional Identity Theft
While synthetic and traditional identity theft are used to achieve the same end - committing fraud - they go about it in slightly different ways. There are a few main distinctions between synthetic and conventional identity theft.
In traditional identity theft, the fraudster uses the victim's complete identity and pretends to be someone else. Typically, fraudsters immediately commit crimes when they gain access to the victim’s identity, such as spending large sums of money on the victim’s cards to exceed their credit limit or making high-value purchases before the victim realizes it.
On the other hand, synthetic identity theft is the creation of a fake person's identity by utilizing various pieces of information, which can be more challenging to detect and has no urgent time frame in which the crime has to be committed.
This type of theft frequently goes undiscovered since there is no apparent victim. (Even though someone’s personal credentials have been stolen, they aren’t actively being exploited for money themselves, so it’s less likely to be found out).
One of the main differences between traditional and synthetic identity fraud is the urgency with which criminals commit fraud. With traditional fraud, criminals feel rushed to commit fraud while they have access. With synthetic fraud, since the customer profile has been fabricated, criminals use the fake identity to commit fraud repeatedly, without the same urgency.
Synthetic fraud can be conducted in a multitude of ways, but the main process is fairly simple. Synthetic identity fraud uses the following steps:
Step 1: Acquire Credentials
Criminals looking to commit fraud often acquire information that can be used to create synthetic identities. This information consists of legitimate identifying information from real people, which will be used to lend credibility to the entire user profile.
Step 2: Create a Fake Identity
Fraudsters then create a synthetic identity composed of both legitimate and fake information. These fraudsters usually use authentic Social Security numbers, addresses, and other information that was stolen or purchased on the dark web.
Criminals often look to create synthetic IDs that won’t raise red flags, such as individuals with no credit history like the elderly, the homeless, and the unemployed.
Step 3: Commit Fraud Using the Synthetic ID
Fraudsters then use the synthetic identity to commit fraud, identity theft, and other crimes. This can take many forms, but the common factor is that criminals use synthetic IDs to commit fraud.
A common tactic is to create an account at a bank and steadily build credit. Once credit has been established, the fraudster applies for credit. The fraudster then maxes out their available credit and disappears.
But synthetic IDs can also be used to open accounts or purchase assets, from insurance policies to real estate, which can then be used to launder money.
Given the fact that these identities use a variety of legitimate credentials, they are often harder to detect. Fortunately, there are several methods organizations can use to detect and prevent them; we cover each below:
Identity Verification
It’s crucial to get in front of the problem. One of the best ways to prevent synthetic identity fraud is to stop fraudsters from opening accounts in the first place. Performing adequate customer due diligence and KYC procedures at the point of onboarding will keep criminals from having the opportunity to exploit an organization.
Businesses should invest in advanced identity verification technologies to ensure that the users they onboard are who they say they are. This should include document verification, as well as more advanced features like biometric or multi-factor authentication.
Customer identity verification software can recognize fraudulent documents using techniques like image recognition, font detection, and database validation.
By preventing fraudsters from onboarding in the first place, FIs take away their ability to commit fraud.
Follow-up Due Diligence
While customer due diligence is often associated with onboarding, it goes beyond that. Synthetic IDs, since they use a combination of fake and real information, are much harder to catch. Despite an organization’s best efforts, these fake accounts can still get through.
It’s a good practice to have enhanced due diligence measures to catch the criminals that get through. Genuine individuals often leave a varied data footprint, which is one of the main differences between real and synthetic IDs. Real people occasionally change their contact information, address, or phone number; while synthetic IDs often remain static.
Real people communicate with family and friends on social media, maintain public and tax records, get parking tickets, and have proof of income. The point is, authentic people leave a data trail throughout their life, which is much harder to falsify with synthetic IDs.
It’s crucial for organizations to conduct customer due diligence, even on existing customers regularly. Validating a user’s ID can limit their ability to commit fraud, and is an ideal way of detecting a synthetic ID.
Transaction Monitoring
Synthetic IDs are designed to be hard to detect, posing major problems for financial institutions looking to identify them. The fact is, despite best efforts, some of these identities will slip through the cracks.
To actually root this out, organizations need to employ oversight even after customers are onboarded and due diligence has been completed. One of the best ways to catch synthetic IDs is to monitor customer behavior for anomalies.
Transaction monitoring is a lucrative tool in this fight, screening transactions for high-value purchases and other unusual or suspicious behavior. This can be used to detect when purchases are being made from locations that don't align with the synthetic IDs address or historical patterns.
Suspicious activity can be flagged for investigation, enabling fraud teams to detect - and stop - synthetic users on a platform.
All a fraudster has to do to commit synthetic identity fraud is use a synthetic identity. Unfortunately, there are many ways a criminal can actually use a synthetic identity.
Below, we look at a few examples of how synthetic ID fraud looks in practice, so you know what to look for.
Max Out Credit and Disappear
Most cases of synthetic identity fraud involve criminals exploiting access to credit, only to disappear without footing the bill.
For this to work, fraudsters often need to perform a ‘long con’, as they need to establish good credit over time (to gain access to higher credit limits and more services).
The fraudster opens an account using the synthetic ID, and then poses as a normal customer. They develop credit over months (or even years) by performing regular transactions. Over months (or even years), the fraudster builds a credit history, establishing good standing with the organization. They then use this to access credit, which they never pay back. This can be in the form of loans, credit cards, online purchases, and more.
Unfortunately, the behavior of these criminals makes it difficult for businesses to track, as the user often attempts to mimic the behavior of a legitimate user for an extended period of time. Organizations will need to leverage behavior monitoring tools that let you analyze user activity to detect fraud better.
Account Takeover
In this case, the fraudster purchases a collection of legitimate credentials online; they have a real person’s SSN, name, and multiple account logins (including passwords). With this information, they can create synthetic IDs. With access to the person’s existing accounts, they can gain control and divert access to their synthetic ID.
They are then able to make a series of purchases with the synthetic ID, sometimes while using the legitimate user's credit card.
Account access is a great way to monitor this. If users attempt to access an account from a new location or a new device, they should be required to pass a verification check. Other features like multi-factor authentication and biometric verification can also provide added security.
False Unemployment Claims
The fraudster creates a synthetic ID using various real information they purchased on the internet. The SSN, name, and previous employment information are all legitimate, but the address, contact information, and some other credentials are all fake. The fraudster then files unemployment claims using this fake identity. They collect claims for a period of time, eventually disappearing only to repeat the process with a new stolen SSN.
Even though the initial identity was legitimate, and there is no individual victim that is being robbed, the legitimate user’s SSN could now be associated with the activity of the fraudster, all without their knowledge.
Diligent customer due diligence during onboarding is essential for stamping this out, stopping fraudsters from making accounts in the first place. Since some fraudsters are adept, some will get through the cracks. The next line of defense is not just monitoring transactions, but user behavior.
Criminals conducting unemployment fraud using synthetic IDs attempt to make this activity appear legitimate for as long as possible, so they will often have seemingly legitimate transaction activity. However, they often fail to have standard behavior of a legitimate user - as these accounts are only used to steal funds. By monitoring account activity using more than just transaction behavior, institutions can flag suspicious accounts and root out this type of fraud.
Stamp Out Synthetic ID Fraud in its Tracks
By nature, synthetic IDs are extremely hard to detect during onboarding, as they are designed to pass basic identity verification checks. And since most fraudsters want to fly under the radar, they often attempt to behave like a legitimate user for a long period of time. After they’ve established credit, they cash out and disappear. Still, it’s important to have a robust onboarding solution that can detect even the most advanced synthetic IDs.
FIs may be able to monitor user behavior to look for abnormalities in a user's behavior over time. Users that have a lot of transfers between a limited number of entities - but not much other purchasing activity - could stand out as fake accounts using synthetic IDs.
For marketplaces, it’s a bit more challenging; fraudsters have built up credit and are looking to use this credit nefariously on your marketplace. Unlike the accounts set up at an FI, synthetic IDs on marketplaces are often used to open accounts that remain active for a short time - just long enough to make fraudulent purchases.
Instead of relying on behavior patterns, marketplaces will need strict onboarding to stamp out fake accounts. Each transaction will need to be authenticated before processing to avoid chargebacks. It’s best to put preventative measures in place, such as limiting total spending within a specified period of time to mitigate fraud losses.
Companies should use high-quality transaction monitoring to identify suspicious activity when it’s happening, and behavior analytics that goes beyond just transactions to truly understand if a user is authentic. Some solutions can even help teams detect and prevent the most impressive fraud schemes, ones powered by AI and machine learning.
Schedule a demo today to see for yourself how Unit21 can help you root out synthetic ID fraud.
Subscribe to our Blog!
Please fill out the form below:
Learn more about Unit21
Unit21 is the leader in AI-powered fraud and AML, trusted by 200 customers across 90 countries, including Green Dot, Chime, and Sallie Mae. One unified platform brings detection, investigation, and decisioning together with intelligent automation, centralizing signals, eliminating busy work, and enabling faster responses to real risk.






.webp)
.webp)
.webp)