The phrase “follow the money” implies that financial crime can be rooted out by tracing illicit transactions back to their ultimate beneficiaries. That’s the idea behind using a process called link analysis for anti-fraud and AML: to visualize and analyze relationships between actors in financial transactions to search for suspicious patterns or anomalies.
Take, for example, a case of multiple online eCommerce accounts with similar names, similar ID credentials, identical payment details, and identical shipping addresses that are all created in short succession.
This would likely suggest some form of fraudulent activity that includes stolen payment information. Link analysis visualizations make these sorts of oddities more readily apparent so financial institutions can shut down the actors behind them faster.
So what is link analysis, and how exactly is it applied in fighting financial crime? Read on to find out.
What is Link Analysis?
Link analysis, also called network analysis, is a method of data analysis that involves examining the relationships between nodes in a data network. It commonly uses data visualizations that make it easy to examine the connections between individuals, entities, and objects.
What is Link Analysis in Banking and Financial Services?
In terms of financial fraud detection, link analysis is primarily used to identify connections between individuals, entities, and institutions involved in transactions. Typically, the more that personally identifiable information overlaps between these actors, the more likely transactions are potentially fraudulent and warrant further investigation. Another likely flag for fraud is if nodes are linked to other nodes that have already been tied to fraudulent activities.
Link analysis is more often used in prosecution, as it’s easier to review connections after criminal financial activity has been identified. However, when paired with proper transaction monitoring, case management, and other risk prevention methods, link analysis can be an invaluable tool for preventing fraud actions.
Benefits of Using Link Analysis
So why use link analysis for fraud detection?
Essentially, link analysis allows for easily conceptualizing the relationships between financial actors, credentials, and transactions. This makes it simpler to pick out patterns or connections that seem out of place, which may indicate fraudulent activity. More specifically:
- Visualizations simplify analysis: Fraud networks are becoming increasingly complex, so it’s very difficult to root them out by studying data in table form. Visualizing data in relational graphs makes connections between pieces of information much easier for people to identify and understand.
- Reduced complexity shortens investigation times: Visualizing relationships in graph form makes more sense to humans than writing them out as words or numbers. So fraud analysts can spot patterns and anomalies much faster, and thus act on them sooner to potentially prevent fraud before it happens.
- Interactive visualizations are scalable: Interactive data visualizations used for link analysis allow for zooming out to a general overview, or zooming in on specific connections. So they make it easier to understand relationships between pieces of data, even when dealing with vast amounts of data from different sources.
- Streamlined risk profile building: By visualizing relationships, link analysis makes it simpler to assess a customer’s financial risk profile by looking at their connections. Ties to nodes involved in fraud or money laundering networks may mean a customer presents too much risk to continue a business relationship with.
How Link Analysis Works
At its core, link analysis in terms of fraud detection involves three main elements:
- Network: A collection of objects, and the relationships between them, that pertain to a particular financial scenario. An example might focus on a corporation and all of the other entities they do business with, such as clients, suppliers, financial institutions, and so on. It may also include all of the institutions that those businesses have relationships with.
- Nodes: Discrete objects within a network. In financial terms, a node could be a customer, a payment method (e.g. a credit card), a physical address, an IP/web address, an account, a registered piece of property (e.g. a car), a digital device, and so on.
- Links: The relationships between objects in a network. Using the previous example of financial nodes, a customer could be known to use a particular payment method, live at a particular address, have accounts at a particular financial institution, own a particular car or device, and so on.
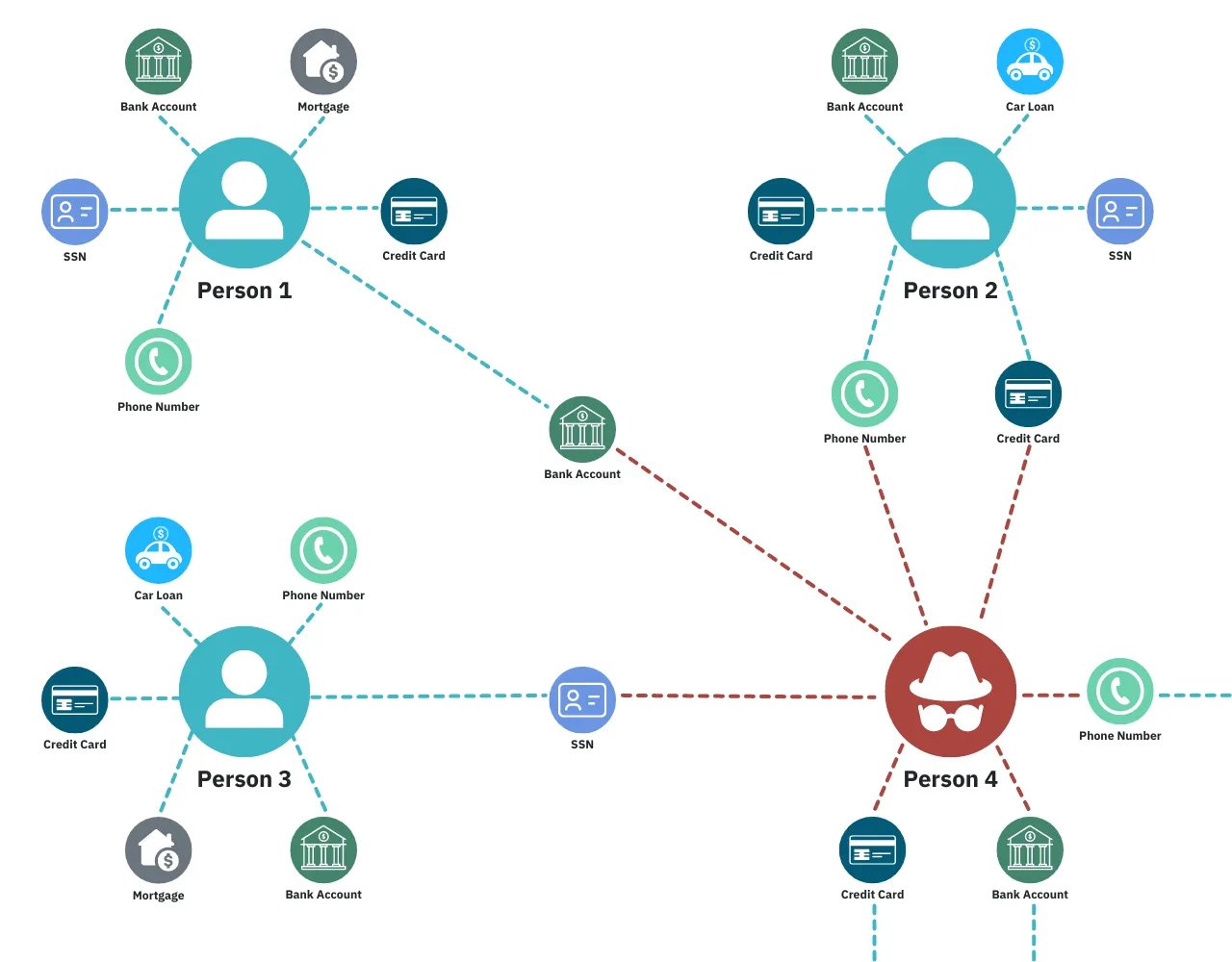
The goal of link analysis in AML is to visualize a network of financial actors and transactions and how they are related to each other.
What are a company’s clients and suppliers? Where does a person typically have items they order online shipped versus where they actually live? Does more than one person use the same payment method, or claim to own the same property? Are multiple sources repeatedly depositing small amounts of money to the same account, potentially to avoid attracting attention?
Through link analysis visualizations, an anti-fraud/AML officer can have all of this information in front of them at once in a simple-to-understand format. This makes it easier for them to pick out unusual patterns or outliers that may suggest fraudulent behavior. Then they can follow up on these leads to see if anything actually suspicious is going on.
How to Do Link Analysis to Detect and Prevent Fraud
Link analysis is a key anti-fraud and AML tool because it simplifies analysis of complex situations by using easy-to-understand visualizations. This helps an anti-fraud/AML agent quickly confirm the presence or absence of suspicious connections or patterns. That’s important when dealing with large caseloads where each case can only take up so much time.
A basic version of the link analysis process for anti-fraud/AML looks like this:
Step 1: Determine the initial scope of the data network
Link analysis is often performed with the intention of answering a specific question. So the first step is to determine the parameters of what information is or isn’t relevant to the problem at hand. This can cut down on the amount of time it takes to sift through data in order to evaluate relationships as being normal or suspicious.
Don’t worry too much about getting this exactly right, though. A link analysis network visualization is often scalable, so it’s completely possible to expand its scope by adding new information that may become relevant later.
Step 2: Collect the relevant data
After defining the scope of the investigated case, the next step is to pull together the data that falls within that scope.
Which individuals, companies, or other legal entities are involved? What are their personal ID credentials and financial assets? Are specific pieces of property involved, such as houses, buildings, cars, or digital devices? Which locations are relevant? What is the value of assets trading hands? These are all pieces of information that need to be incorporated so connections can be built between them.
Step 3: Visualize the network
Once the relevant data has been assembled, it’s time to put the pieces in place and draw the connections between them. Link analysis software is typically used for this, as it automates a large portion of the process.
It can also be scaled up so that if something suspicious is found in one of the later steps, more data can be added to flesh out the network surrounding the anomaly to see how far it extends. In this way, identifying one instance of fraud can uncover a whole network of fraudsters.
Step 4: Analyze links between nodes for patterns and outliers
Having all of the data and connections involved in a particular case in front of an anti-fraud/AML agent at once makes it simple for them to spot anything suspicious or out of place. They can use their own training and deduction skills, or perhaps get assistance from link analysis tools that have been trained through machine learning to recognize patterns that typically indicate criminal financial activity.
Step 5: Follow up on anything that looks suspicious
Just because link analysis uncovers a suspicious connection (or pattern of connections) doesn’t necessarily mean that it represents anything criminal. It’s important to follow up with the parties involved in the transaction(s) and see if they can account for the relationships and oddities discovered. If they can’t, then it’s a serious red flag that they’re involved in shady business.
Leverage Link Analysis for Deeper Insights
The fact is, the more information you have at your disposal, the better you’ll be at detecting and preventing fraud. Link analysis empowers risk and compliance teams with rich data visualizations, enabling professionals to make better decisions faster.
Learn more about Unit21
Unit21 is the leader in AI-powered fraud and AML, trusted by 200 customers across 90 countries, including Green Dot, Chime, and Sallie Mae. One unified platform brings detection, investigation, and decisioning together with intelligent automation, centralizing signals, eliminating busy work, and enabling faster responses to real risk.


