
.webp)
If you have ever seen a movie featuring a bank robbery (or hopefully have not been in one in situ as a retail bank worker), you know the power of the silent alarm. Once that button is hit, authorities are notified without the "bad guys" knowing the authorities are on their way.
But did you know that other "silent alarms" may be buried in your organization's data? Let's look at action-based events that can provide real-time indicators of potentially fraudulent or unauthorized activity.
Consistent Fraud Monitoring, Account Dormancy, & Precise Data Points Key for Fraud Prevention
This is our sixth installment in Fraud Files, our blog series that shares unique insights based on data from over 4.05B events on the Unit21 platform. In our previous posts, we explored several trends and insights, including:
- Part 1: The rate of true positives for fraudulent events for accounts in their first 90 days
- Part 2: The differences between banks and credit unions on fraud activity detected in their first 14 days
- Part 3: Why keeping an eye on account dormancy is as essential as monitoring account action
- Part 4: A look into recent fraud trends by top rules created
- Part 5: The reasons why precision in data points combined with graph-based rules sharpens fraud detection.
Action-Based Events - the Silent Alarms
Action-based events are any user-initiated actions within a system that can be monitored and analyzed for fraud prevention. These include, but are not limited to, login attempts, password changes, address updates, and user or account details modification. When we talk about action-based events, we often speak of specific actions that appear harmless enough on the surface, yet for risk and fraud teams, they give us a lot of insight. The significance of these events lies in their ability to help you proactively identify and prevent fraudulent activities before the actual financial transactions occur.
Our data shows the distribution of non-transaction action-based events used in rules by Unit21 customers. This data can help you see some of the latest trends in how modern organizations use alternative data points beyond transaction data to improve your rules and detect more fraud.

Monitoring Login and Account Changes Events
Login events: More than 62% of all action event-related rules are related to login events. We've all done it before - with the myriad of usernames and passwords we must remember for every account, it is hard to keep track of which one requires which login info. Multiple login attempts can be just that. However, this pattern can also indicate a brute force attack, where a fraudster is trying to guess the password. Once in, they will lock out a legitimate user.
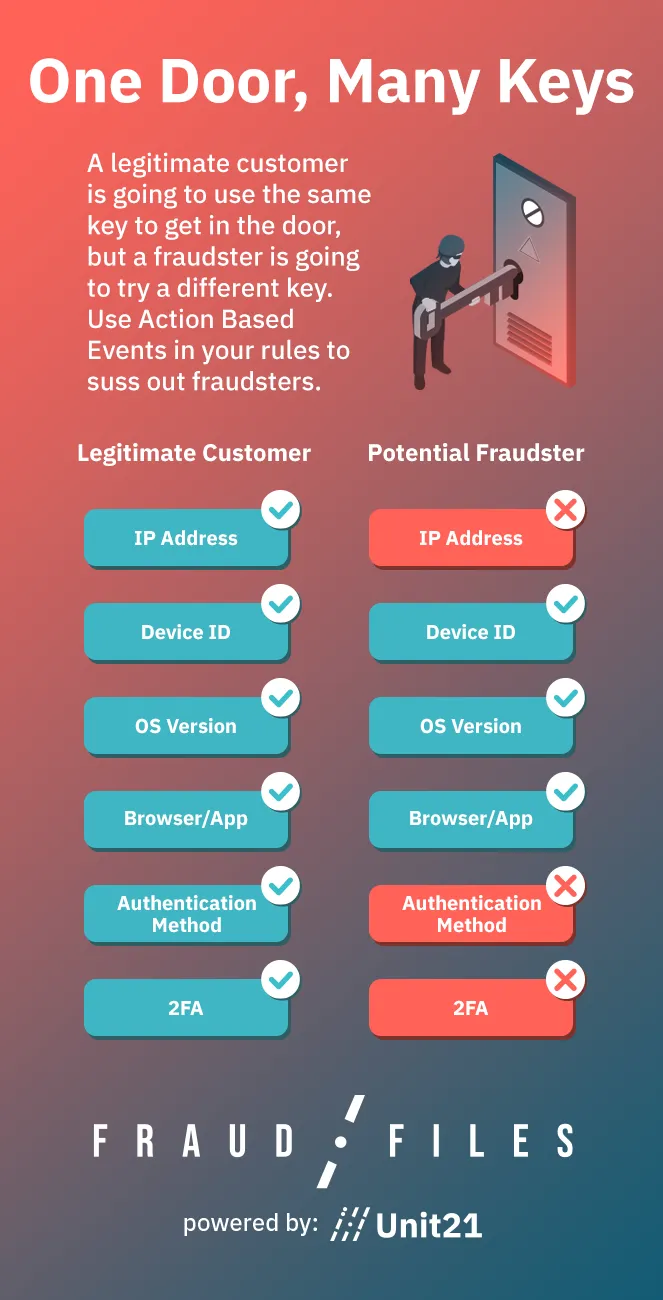
Account changes: Nearly 12% of rules with action events are related to user or account changes. Updating contact information is a routine account management activity. Yet, if done shortly after account creation or following a series of transactions, it might suggest a fraudster attempting to reroute communication and intercept authentication messages or transaction alerts.
New account: At 9%, we see our customers establishing rules related to new account activity. This activity can include a new user sign-up, adding a new account, or linking a new funding source like a bank account.
For example, the user adds several payment methods or bank accounts to their profile shortly after the account setup. It's common for users to link a bank account or credit card, but adding multiple payment methods in quick succession could indicate a fraudster's attempt to test which stolen financial details are valid and unblocked.
Multi-factor authentication (MFA): Nearly 9% of the action events are related to MFA. Activating 2FA is a security best practice. However, if the phone number used for 2FA activation is disposable or virtual (which can be identified through certain verification services), it may suggest a fraudster's attempt to maintain access to the account even after the initial theft or misuse is discovered.
In the ‘other’ category of the pie chart, there are multiple events, including but not limited to addressing changes immediately after account setup or shipping of a product, changing account security settings, card and pin transactions, and more.
Incorporate Action-Based Rules in Your Rule-Based Monitoring System
Understanding the nuanced landscape of action-based events provides fraud fighters with a powerful lens through which to detect and prevent fraud. Vigilant monitoring across a variety of non-transactional activities, such as login behaviors, account changes, and the setup of new accounts, which are sometimes overlooked, can act as early indicators of fraudulent intent. The actionable takeaway for fraud teams is leveraging this data to refine and enhance your rule-based monitoring systems.
By incorporating a broader spectrum of action-based indicators—especially given the predominance of login events and the subtleties of account modifications—fraud prevention strategies can become more proactive and adaptive. This means developing dynamic rules that catch traditional fraud signals and adapt to emerging patterns in real-time.

In doing so, financial institutions can significantly tighten their security net, making it increasingly difficult for fraudsters to exploit system vulnerabilities, thereby safeguarding their operations and customers' trust. So when that (silent) alarm sounds, you know you are listening.
Subscribe to our Blog!
Please fill out the form below:
Learn more about Unit21
Unit21 is the leader in AI-powered fraud and AML, trusted by 200 customers across 90 countries, including Green Dot, Chime, and Sallie Mae. One unified platform brings detection, investigation, and decisioning together with intelligent automation, centralizing signals, eliminating busy work, and enabling faster responses to real risk.



