Fraud is hard enough to deal with as is, even when it’s a known threat and a common tactic that is readily identifiable.
But what do companies do if the actual threat is posing as the solution? What do companies do when the threat is masquerading as the anti-fraud security provider?
These threats, known as scareware, pose a major threat to businesses—and their customers. Below, we explore what scareware is, how it works, and how organizations can prevent scareware attacks.
What is Scareware?
Scareware is a form of malware that causes fear, anxiety, and urgency to trick users into downloading unwanted software. Often, this action involves buying non-functional software that doesn’t offer any real value or malicious software that further infects the victim’s device.
Ironically, many scareware schemes actually claim to be security programs themselves. Through a series of pop-ups and prompts, they convince the victim that they are already being attacked, and then offer them a ‘solution,’ which is actually a non-functional software or is itself malware (that will be used to further exploit the victim).
To do this effectively, scareware solutions often present themselves as security services and providers, mimicking traditional security messaging and sometimes even copying logos to make the prompts look more legitimate and convincing.
With non-functional software, the user essentially pays for a software they think is fixing the infection on their device, when in fact it’s an entirely fake ‘solution’ to the scareware threat. The scareware developer makes off with the amount the victim pays for this fake software, and the user never knows any better.
With malware, the user actually uses scareware as an impetus to get the victim to download malware. In these cases, the scareware is often not used for any ‘gain,’ aside from getting the malware installed on the victim’s device. Once the victim runs the malware, the fraudster can steal their personal data, ransom their information or device access, and otherwise exploit the victim.
Scareware can be used to extort a victim for financial gain, infect a victim’s device with malware, commit pranks on the victim, and more.
Ransomware vs Scareware
Both ransomware and scareware are forms of malware. Each is its own specific type of malware, and each operates differently.
- Scareware: Uses social engineering to ‘scare’ the victim into downloading a non-functional or malicious software that will be used to commit further acts of fraud.
- Ransomware: Uses cryptoviral extortion to control access to the victim’s electronic device and/or personal information. The fraudster then demands a ransom in exchange for unlocking access to the victim’s device or to stop the fraudster from revealing the private information publicly.
The common denominator is that both prey heavily on the victim’s fears.
While they aren't technically the same thing, scareware is commonly associated with ransomware, as many scareware attacks lead to the use of ransomware. In this scenario, scareware is used to scare the victim into installing ransomware, and then the victim is exposed to a traditional ransomware scheme. In this case, though, ransomware, and not scareware, is used to gain illicit funds from the victim—despite scareware facilitating the entire process.
How Does Scareware Work?
Scareware prompts a user to take a specific action—most commonly downloading an unwanted (and often non-functional or malicious) software. In the end, the victim loses money, has a device that is now infected with malware, and has their information compromised.
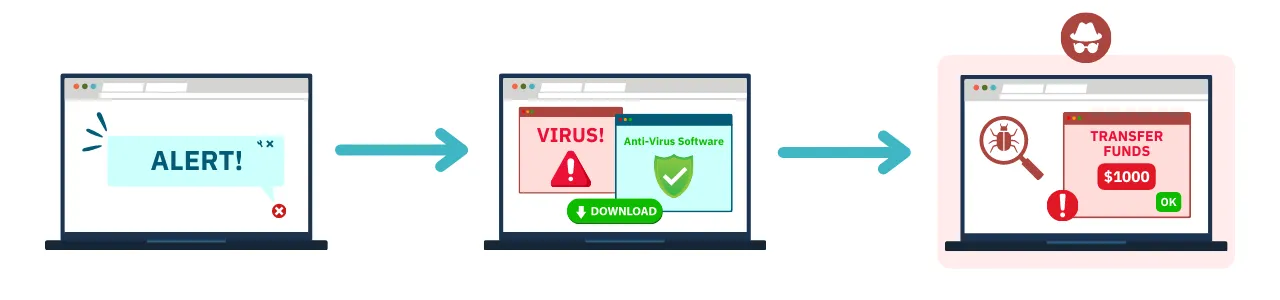
In general, scareware schemes follow a few basic steps:
- The fraudster targets the victim with a series of alerts (pop-ups, emails, and more), prompting the user to download a software. Typically, these take the form of fake security alerts from fraudsters posing as legitimate security providers.
- The victim either (A) is prompted to buy a ‘solution’ to the problem the alerts warn of, or (B) the victim is prompted to download a free software by clicking a link or submitting information in a form.
- The victim either (A) pays for the fake software solution, which appears to solve their problem, or (B) clicks a link (intentionally or unintentionally) to download the free software solution, which instead installs malware on their device.
- The fraudster either (A) stops serving the victim scareware adds and makes off with the cash they paid to ‘fix’ their problem, or (B) uses the malware to commit further acts of fraud against the victim, stealing their personal information or extorting users to regain access to their device.
The tactics used to prompt someone to click these links are varied—and often pretty adept. Scareware threats can come through email, social media, or even from visiting a certain website. They can be disguised as advertisements, security alert warnings, and much more. Some even automatically download as soon as a pop-up is triggered, an email is opened, or a link is clicked, giving the user very little recourse to stop the threat.
Many scareware schemes involve posing as a security provider and sending alerts to the victim that make them think their device is infected. The user then sells them a ‘solution’ in the form of a device cleaning and security software. The solution either does nothing or is itself malware, designed to further exploit the victim. This can expose victims to further threats, such as identity theft, impersonation, or account takeover fraud.
Some scareware developers have gotten very good at mimicking the design, style, and language of legitimate security providers—making it hard to distinguish these attacks from legitimate threats.
How to Prevent Scareware Attacks
For organizations, the challenge of preventing scareware attacks lies in the fact that a lot of the power is in the hands of the individual user. After all, they are the ones that have to click the link, open the email, or visit the website that exposes them to scareware.
After that point, they must notice they have it and then take action to clear their device of the threat and any subsequent threats they’ve been exposed to, such as data breaches and malware.
Really, there is little an organization can do to intervene in this process. For organizations to meaningfully prevent scareware attacks for their users, they need to try to exercise control over the areas they do as much as possible.
Fortunately, there are a few areas where organizations can impose some preventive and protective measures, which we cover in more detail below.
Establish Adequate Security Measures & Systems
Organizations will want to do everything possible to stop scareware from spreading from their platform. This means having property security measures in place—teams need to take the proper steps to protect their systems (and organization) from any security breaches.
Real-time security protocols should be operating around the clock to keep your system—and customers—safe. More importantly, staff needs to be adequately trained on how to use these systems and how to properly mitigate security threats when they occur.
Verify Partnerships, Integrations, and Extensions
First and foremost, limit your platform’s exposure by being careful about the partners you choose. Only use trusted partners that you’ve verified.
This means controlling the products, features, and extensions you expose your users to—to be extra diligent, this should extend to advertisements as well. Even if you allow malvertisements unintentionally, it can still affect your reputation if customers are exposed to scareware schemes because of ads you allowed on your platform.
Analyze Customer Behavior for Anomalies
Analyze behavior gleaned from data monitoring tools to see drastic changes in customer behavior—changes that may have gone unnoticed.
Major changes in how users are behaving could be a signal that your platform (and your users) have fallen victim to scareware, especially if many users make strange account changes (at a far higher rate than before), abruptly stop conducting business, or otherwise act outside the norm. These anomalies can signal when scareware schemes are being conducted, suggesting a revision—and revamping—of security measures and fraud controls.
Educate Customers on the Potential Threats
When you educate your customers on how to protect themselves, you keep both them—and your organization—safe from fraudsters.
The fact is, there is only so much organizations can do to stop scareware threats, since the customers often have to initiate the process themselves. Most prevention comes from seeing the signals of a potential scareware threat and avoiding it in the first place—and in almost all cases, that interaction happens on the customer's end.
It’s important to educate customers on the potential scareware threats, how they appear, and what should be done if they think they may be under attack.
Below, we cover some basic practices to keep consumers safe:
- Don’t click on any unknown links or malware notifications
- Keep your operating system and browsers updated
- Use a reliable, trustworthy antivirus program
- Enable pop-up blockers and other security measures
- Research a particular software or tool before you download it
- Only rely on recognized, trusted cybersecurity providers
- Don’t just close the pop-up, close the entire browser window
- Don’t open emails from unknown senders or with strange subject lines
Examples of Scareware Scams
To illustrate just how varied and prominent scareware attacks are, we’ll take a look at three real-life examples of famous scareware attacks.
NightMare
One of the first known scareware programs to be distributed was developed by Patrick Evans in 1990. The program, named NightMare, would lie dormant on a victim’s PC. It would activate randomly, running in the background.
Intermittently, the entire screen would change to an image of a skull with a bullet hole dripping blood, and an audio recording of a shriek would play. Quite literally, the program was meant to scare the user.
Unlike the more exploitative scareware tools used today—designed to steal from their victims, this program was designed simply to scare the user. Often, these types of scareware attacks are labeled ‘prank scareware’. While still harmful to many, users weren’t extorted for money or duped into downloading malicious software.
Pater Sahurovs
In early 2010, the Minneapolis Star Tribune ran Best Western ads—an ad campaign that was, in fact, a malvertising campaign designed to direct users to fraudulent websites and get them to install malware on their devices.
As is the case with many of these scams, the attack created a series of pop-ups that alleged that the users device was infected, and they could remove the threat and clean the computer by downloading a (fake) anti-virus software for $49.95. Before the perpetrator, Peteris Sahurovs, was caught, they were able to amass $250,000.
Despite the company serving the ads not being involved, this type of breach can result in serious ramifications to a business’s reputation. Organizations must be extremely careful when vending third-party vendors and integrations they support, as well as the advertisements they allow on their platform.
Office Depot and Support.com
Shockingly, even corporations can conduct these types of scams as well. In March of 2019, Office Depot and Support.com settled with the FTC to the tune of $35 million after allegedly exploiting a “PC Health Check Program.” First, customers were deceived into downloading the ‘check’, which would then be used to sell diagnostic and repair services.
While in this case, the software being downloaded is necessarily non-functional in the traditional sense of scareware scams—but it isn’t actually required by the customer in the way that the PC Health Check Program would claim. This tactic drove up sales of the product when many of the customers never required the software in the first place.
In any case, where the customer doesn’t actually need the product being offered, this is essentially a form of scareware.
Protect Against Scareware Attacks with Unit21
Protecting your organization (and its customers) from scareware threats is no easy task. You need to have proper security measures in place, including adequate encryption, firewalls, and other basic security protocols. However, scareware threats work by exploiting the customer—and (despite putting as many preventative controls in place) you can’t control everything the customer does.
Data monitoring that analyzes user behavior is the best way to notice shifts in patterns that may signal customers have been subjected to scareware attacks—but even that has its challenges. It will be difficult to define rules that identify this threat accurately and will likely require testing new rules and fine-tuning existing ones.
It’s essential that teams train employees on how to detect and address these threats, as well as inform customers on how to watch out for them—and what to do if they think they’ve been exposed.
Schedule a demo today to learn how Unit21’s data monitoring solution can help your organization catch any fraud threat—even scareware attacks!
Learn more about Unit21
Unit21 is the leader in AI-powered fraud and AML, trusted by 200 customers across 90 countries, including Green Dot, Chime, and Sallie Mae. One unified platform brings detection, investigation, and decisioning together with intelligent automation, centralizing signals, eliminating busy work, and enabling faster responses to real risk.


