
.webp)
Most teams view ACH fraud as account-level issues like stolen credentials or phishing, but the fastest-growing threats lie in everyday business processes. As ACH use for payroll and vendor payments rises, fraudsters are targeting file-level and process-level weaknesses.
It is no longer just about account takeovers. It’s about who can quietly manipulate routine files before they hit the ACH rails. With NACHA 2026 rule changes, institutions will now be held accountable for internal control gaps, not just external attacks.
Read on to learn how vendor and payroll diversion fraud works, what NACHA 2026 requires, and strategies for ACH fraud detection and prevention.
What Is Vendor and Payroll Diversion Fraud?
Vendor and payroll diversion fraud involves redirecting legitimate payments to attacker-controlled accounts. The danger lies in how seamlessly it blends into existing payment flows. Common methods include:
- Vendor Impersonation: Fraudsters impersonate existing vendors and submit fraudulent banking instructions to trick employees into updating account details.
- Payroll File Tampering: Attackers redirect employee salaries to accounts they control by altering direct deposit information before payroll is processed.
- System Access Exploits: Fraudsters use compromised employee credentials to modify files or payment templates
Why ACH Is the Ideal Rail for Vendor and Payment Diversion Fraud
ACH workflows inherently rely on internal processes and system-generated files. Factors that increase those risks are:
- Large Volumes: Growing ACH volumes across payroll, vendor payments, and recurring transactions can hide small changes in high-volume batches.
- Fewer Real-time Controls: ACH is designed for scheduled settlement rather than instant verification, allowing fraudsters to exploit the delay and manipulate files before transmission.
- Delayed Detection vs. Wire: Unlike wire transfers, where suspicious activity is often identified quickly, ACH issues frequently surface only after settlement.
How Fraudsters Manipulate the Vendor and Payroll Process
Fraudsters exploit predictable operational behaviors, knowing exactly where integrity gaps exist. Key weaknesses include:
- Single Approver Risk: The lack of dual approval or out-of-band verification enables attackers to reroute entire payment runs.
- No Anomaly Detection: Many ACH systems validate formatting but cannot flag unusual routing or account changes.
- Over-Reliance on Email-Based Payment Instructions: Fraudsters spoof vendors, mimic signatures, and time requests to slip past notice.
- Absence of Real-Time Monitoring: Delays between file upload and ACH transmission give fraudsters time to swap files, adjust line items, or inject changes.
Mini Case: “The ACH File Was Clean — But the Routing Was a Lie”
A mid-sized bank reviewed a payroll file that passed all formatting and transactional checks. Amounts and employees were correct, and the file structure was valid. Yet three high-earning employees had their direct deposit routing numbers changed minutes before transmission from a device that had never accessed the payroll dashboard.
This highlights that effective ACH fraud detection must monitor behavioral and procedural anomalies, not just formatting. NACHA 2026 rule changes aim to close these internal control gaps.
What NACHA 2026 Rule Changes Will Require From Institutions
NACHA 2026 is designed to address the rise of deceptive, file-level manipulation, especially where transactions appear authorized but were initiated under false pretenses. Key regulatory shifts include:
- Control Accountability: Institutions must show that internal controls are properly designed, regularly tested, and resistant to overrides or manipulation.
- Authorized but Deceptive Transaction Detection: Institutions must detect and prevent transactions that appear legitimate but are actually fraudulent.
- Anomaly Detection Capabilities: Institutions must monitor for unusual behavior, such as unexpected device access, irregular file edits, or deviations from normal payment patterns.
Are Your ACH Controls Audit-Ready?
Ask your team:
- Are real-time file-integrity checks in place to detect edits before submission?
- Can you validate the source, device, and session generating the file?
- Do you monitor authorization workflows to instantly flag abnormal approvals?
- Do you apply behavior-driven risk scoring for high-risk edits?
If your answer to any of these isn’t an immediate “yes,” then your institution is not yet aligned with NACHA 2026 expectations, and it’s time to close that gap.
Vendor & Payroll Diversion Detection and Prevention Strategies That Actually Work
The most effective defense against vendor and payroll diversion fraud is a multi-layered, automated ACH fraud detection and prevention system that monitors context, behavior, and anomalies in real time.
Key strategies include:
- Cross-Source Data Ingestion: Connect user behavior, devices, and system activity to spot mismatches, unusual changes, and risky patterns before they impact payments.
- Real-Time Anomaly Rules: Monitor routing numbers, file sizes, and out-of-pattern user behavior to detect fraud even when ACH files appear legitimate.
- Behavioral Profiling: Track employee and vendor actions to identify suspicious activity, such as off-cycle payroll changes, vendor updates outside their normal patterns, or unusual system access.
Common ACH Detection Misses
Even the most advanced ACH fraud detection controls can miss subtle signs of fraud if common gaps aren’t addressed. Here are some frequent detection misses institutions should watch for:
- New Devices: Allowing file edits from previously unused devices creates easy entry points for attackers.
- Session Context: Ignoring internal dashboard activity can let suspicious behavior slip through the cracks.
- Blind Trust: Treating all ACH files as legitimate makes it easier for high-risk changes to go unnoticed.
How Unit21 Fills the Gaps in Vendor & Payroll Diversion Detection and Prevention
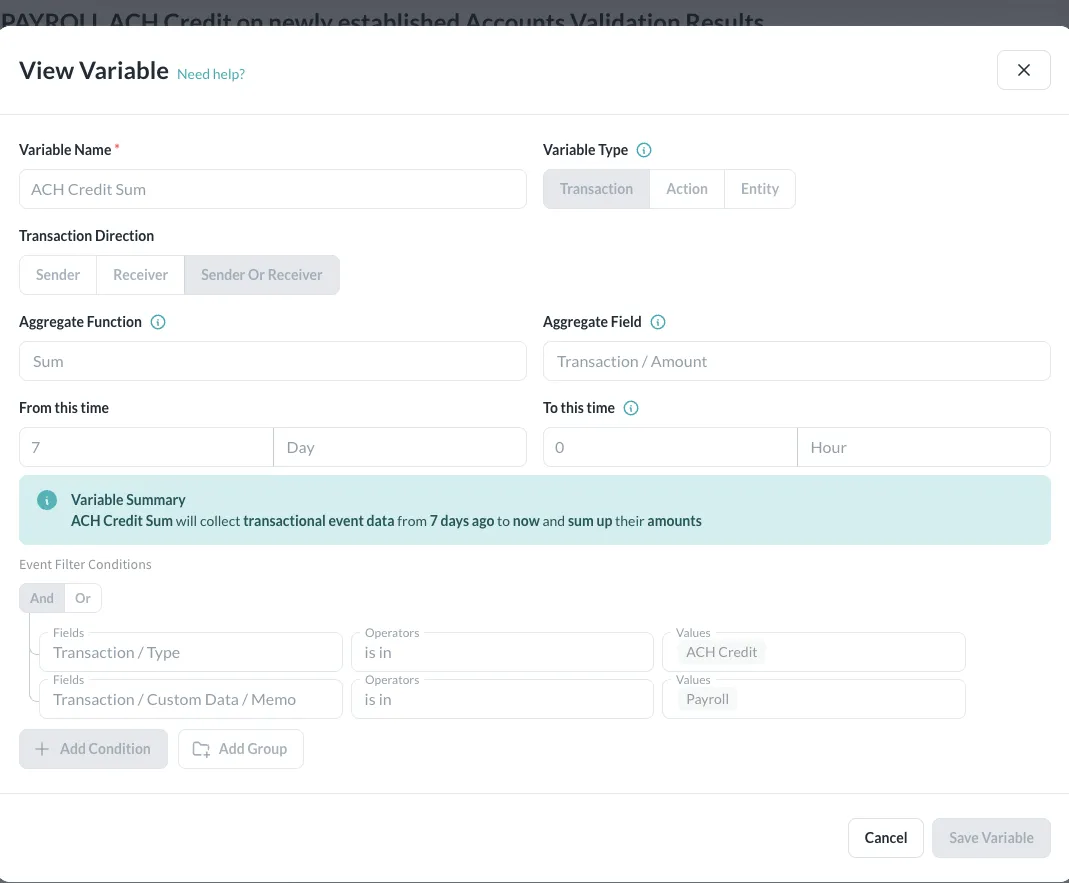
Generic rules and rigid watchlists miss the subtlety of today’s hybrid attacks. Unit21’s platform is purpose-built to detect the cross-cutting signals that indicate vendor impersonation and payroll diversion fraud:
- Unified ACH Fraud Detection: Unit21 consolidates user activity, device fingerprinting, session behavior, and ACH file content into a single detection framework.
- Anomaly Detection Around File Submission: Unit21 triggers alerts based on file submission behavior and content, analyzing how the file was created, who interacted with it, and whether edits or routing changes match normal patterns.
- No-Code Rule Changes: Unit21 lets teams deploy new ACH fraud-detection rules instantly, with no coding required, enabling rapid responses to emerging fraud tactics.
Take Action Against Vendor and Payroll Diversion Fraud Today
Vendor impersonation and payroll diversion fraud are becoming increasingly sophisticated as ACH volumes and automated workflows grow. NACHA 2026 rule changes set a new standard for internal control accountability, requiring institutions to detect not just unauthorized transactions but subtle manipulations that enable authorized yet deceptive payments.
If you want to understand exactly where your institution is exposed, or test whether your ACH controls meet NACHA’s emerging expectations, Unit21 can help.
Let’s walk through your control checkpoints and detection posture. Book a strategy session with Alex today.
Subscribe to our Blog!
Please fill out the form below:
Learn more about Unit21
Unit21 is the leader in AI-powered fraud and AML, trusted by 200 customers across 90 countries, including Green Dot, Chime, and Sallie Mae. One unified platform brings detection, investigation, and decisioning together with intelligent automation, centralizing signals, eliminating busy work, and enabling faster responses to real risk.



.png)
.png)
.webp)
