Stop Fraudsters, Not Customers
Deliver proactive protection against real-time threats by dynamically creating rules based on changing situations, use cases, and risk tolerance in real-time, tailored to you.
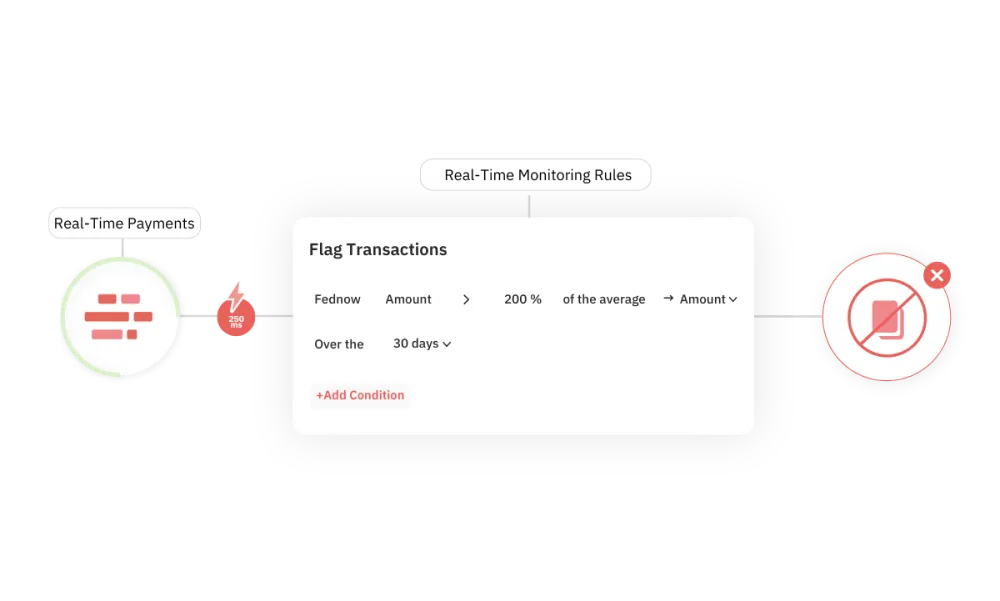
A Comprehensive Fraud Solution
That Puts You in Control
Bring In Any Data You Want
Quickly ingest any type of data—transactional, device signals, user activity, or custom data—to build an accurate journey of the customer.
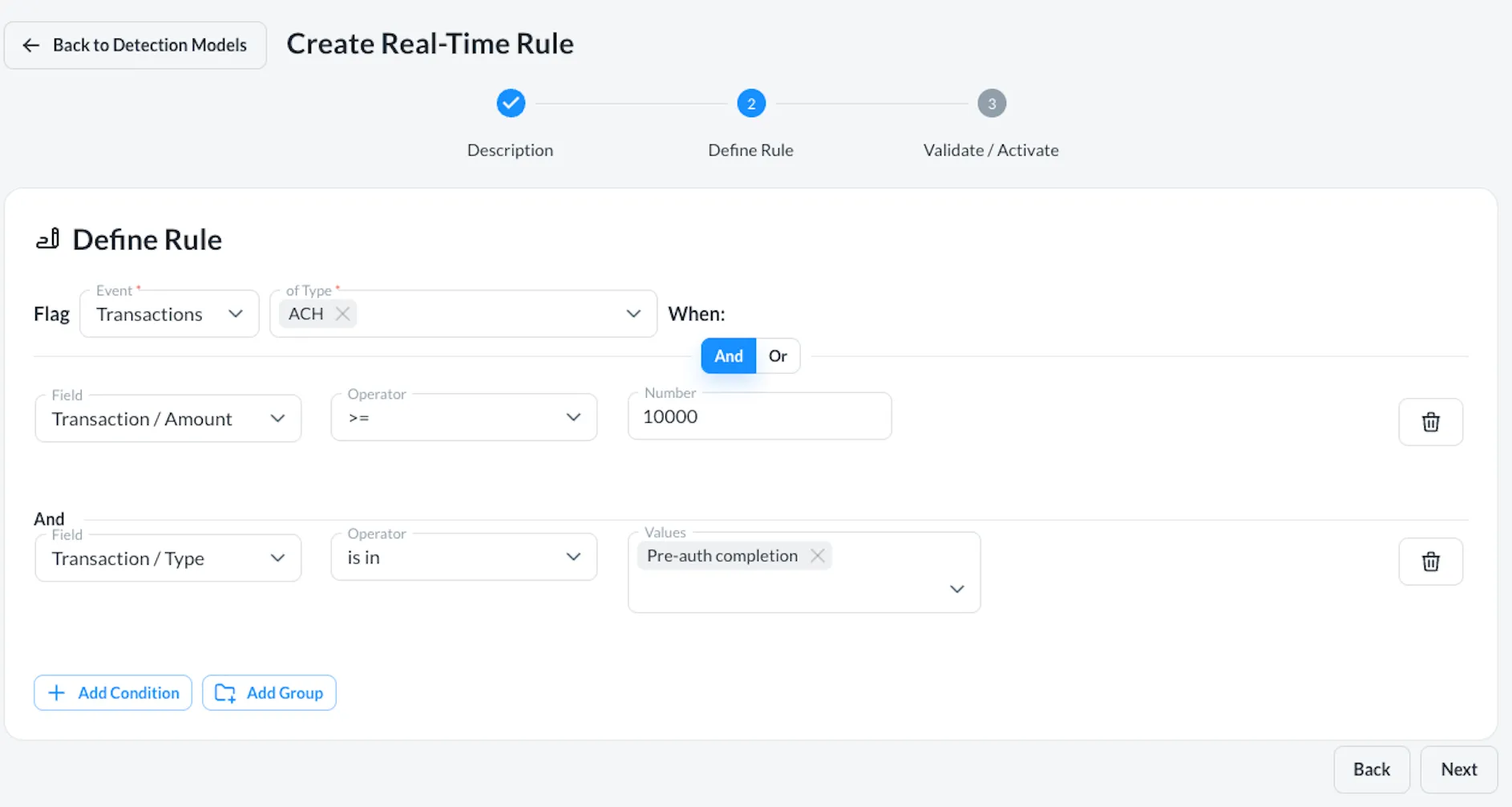
Choose Out-of-the-Box Rules or Create Your Own
Leverage ready-made fraud typologies or create customized rules that align with your unique workflows and risk tolerances.
Test Against Historical or Fresh Data
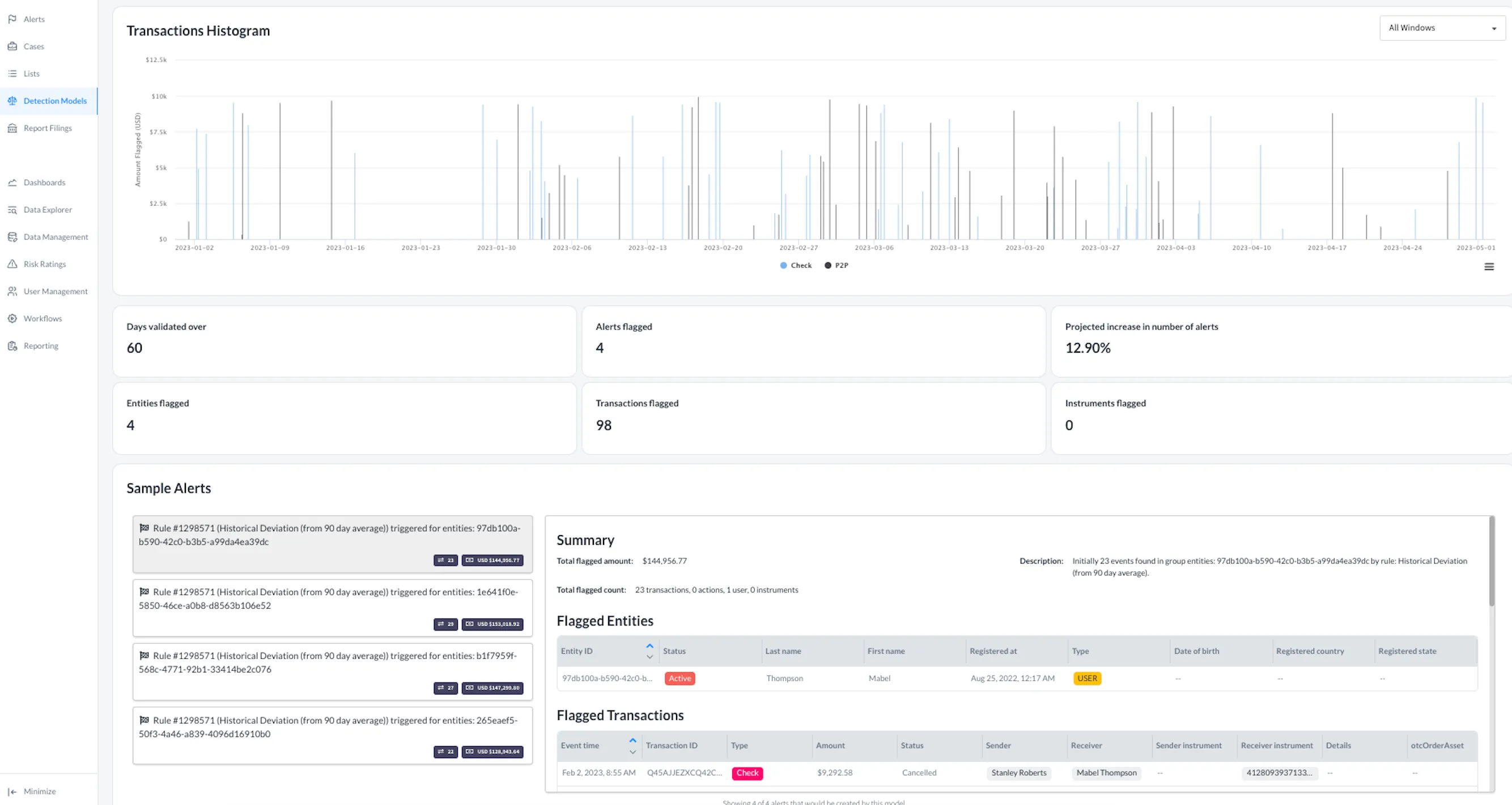
Validate and fine-tune rules by testing them on historical or new data to ensure optimal performance before deployment.
Block Activity Instantly or in Batches
Use sub-second latency for real-time decision-making or batch processing for bulk actions.
Create Allowlists for Trusted Users
Enhance accuracy by maintaining allowlists for verified users, reducing false positives and ensuring a smooth experience for trusted customers.
Time is Money. Make Swift Decisions in Under a Second.
Fraud Doesn’t Wait Overnight, Neither Can You
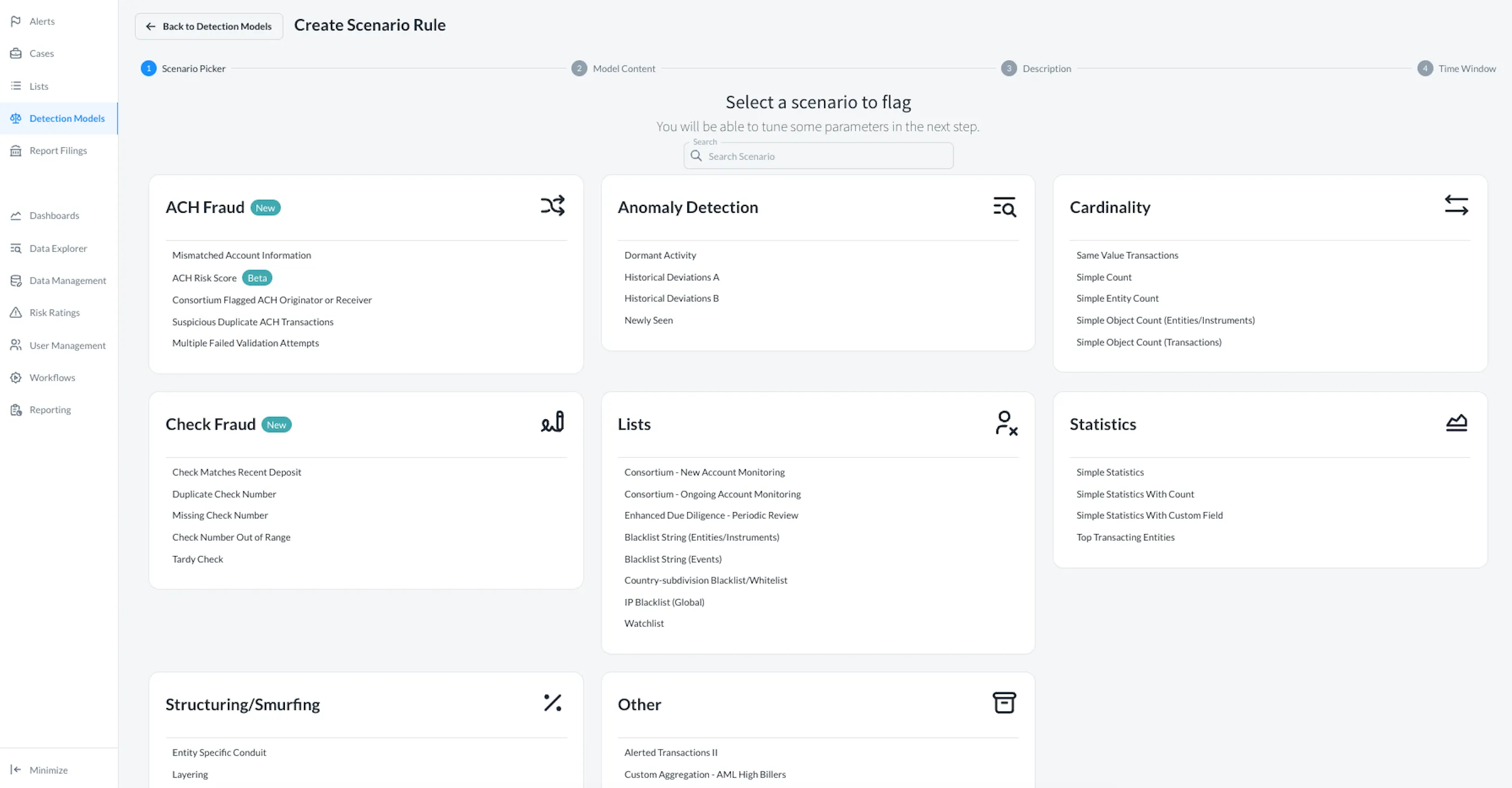
Solve All Fraud Schemes in One Place
Ensure Accuracy & Confidence With Backtesting
Velocity Rules for Early Pattern Detection
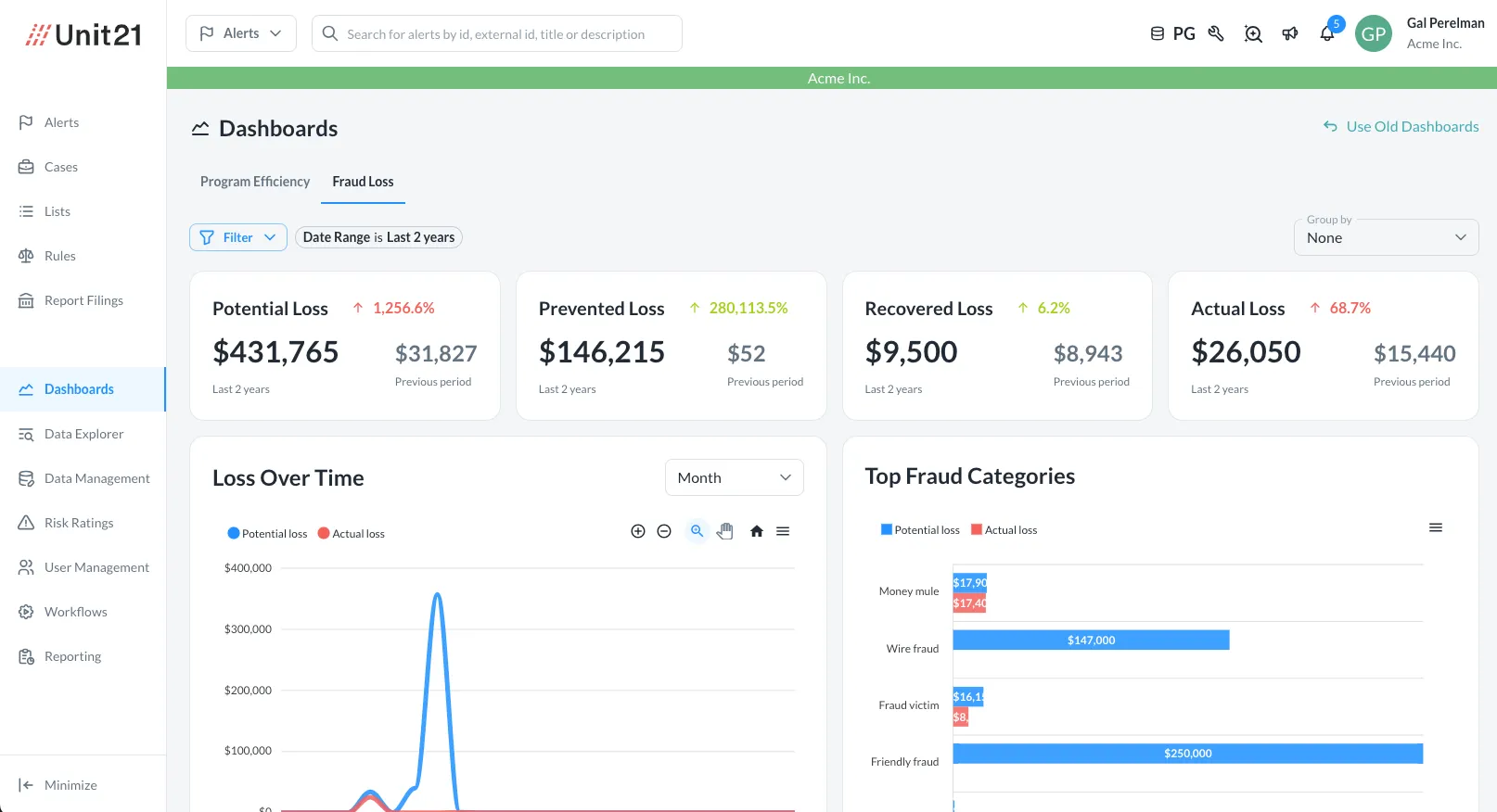
See Every Loss, Every Win, in Real Time
AI-Powered Detection for Suspicious ACH Activity
%20(1).webp)
Device Intelligence delivers real-time defense & measurable impact
Spoofed logins and high-value transfers caught before funds leave.
A fraudster gains access to a business account using a familiar but previously flagged device. They initiate a large ACH transfer to a new recipient - just minutes after changing the account’s contact information. Device Intelligence detects mismatched location data and IP address anomalies, while Unit21’s Real-Time Rules flag the transfer due to risk factors like recipient novelty, amount, and behavior pattern. The transaction is held automatically, giving the team time to intervene before funds leave the account. The AI Agent auto-generates a SAR draft, referencing device risk and impersonation indicators.
Stopping Scaled Credential Abuse
An alert flags dozens of accounts accessed from the same device. Unit21’s Device Intelligence detects a “high-velocity” fingerprint—used across an implausible number of users—alongside several accounts logging in from an unusually high number of devices. Classic signs of credential stuffing. Real-time rules trigger instantly, and Network Analysis maps shared fingerprints and IPs—uncovering a coordinated fraud ring. Unit21’s AI Agent accelerates the investigation by summarizing key behaviors and linking related accounts, reducing review time by up to 80%.
LEARN MORELinked devices reveal hidden mule activity across user accounts.
Late-night transfers begin trickling out from a series of consumer accounts. Each sends small payments to recently added recipients, often with vague memo lines. Device Intelligence identifies that all accounts were accessed from the same obfuscated device using a VPN. Real-Time Rules link the activity across entities, detecting velocity and behavioral anomalies. A graph-based investigation reveals the accounts are part of a coordinated mule network funneling funds to a single endpoint. Unit21 surfaces the risk, escalates cases automatically, and streamlines compliance review with AI-powered summaries.
LEARN MOREDetect, investigate, and comply— faster than ever
An alert flags dozens of accounts accessed from the same device. Unit21’s Device Intelligence detects a “high-velocity” fingerprint—used across an implausible number of users—alongside several accounts logging in from an unusually high number of devices. Classic signs of credential stuffing. Real-time rules trigger instantly, and Network Analysis maps shared fingerprints and IPs—uncovering a coordinated fraud ring. Unit21’s AI Agent accelerates the investigation by summarizing key behaviors and linking related accounts, reducing review time by up to 80%.
LEARN MORE